Getting rid of the Buma Stemra ransomware malware
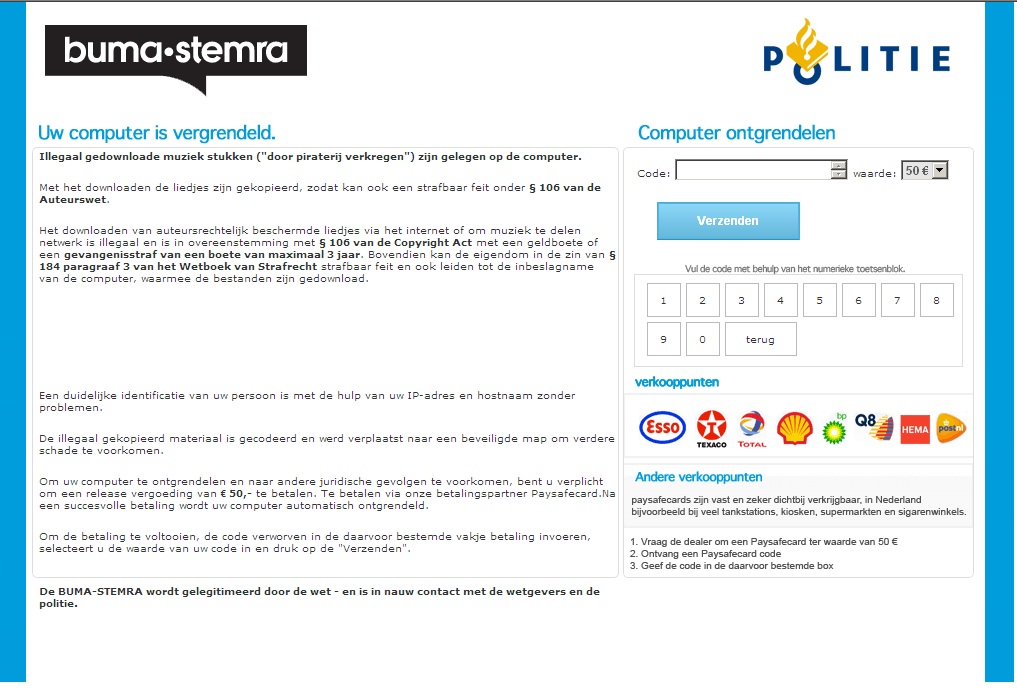
Since a week or so a new Dutch version of some ransomware malware is active in the Netherlands. This malware claims to be from The Buma Stemra, but of course has nothing to do with the real Buma Stemra. The malware successfully takes over the system by replacing the start of explorer.exe with itself, so as soon as the system starts the malware will be loaded instead of the normal Windows environment. The malware further disables editing the registry, accessing the task manager and getting access to the system in any way. When infected with the malware you can not access your own system anymore, the only thing the system will do is show the screen below.
Some news coverage of this malware can be found on WebWereld and a nice overview of how to get rid of this malware can be found on pcwebplus.nl. The approach on pcwebplus.nl includes starting your system from the Kaspersky boot CD, which is a good approach, but it needs you to be able to download this boot CD and be able to burn it. The approach described in this article is mostly based on the approach described on the pcwebplus.nl website, but it shows a way of cleaning your system without having to boot from a boot CD. This approach has been tested on Windows XP, the approach for Windows 7 can be found here. At the end of this page there is a video showing all the steps.
Step 1: Get access to an explorer window
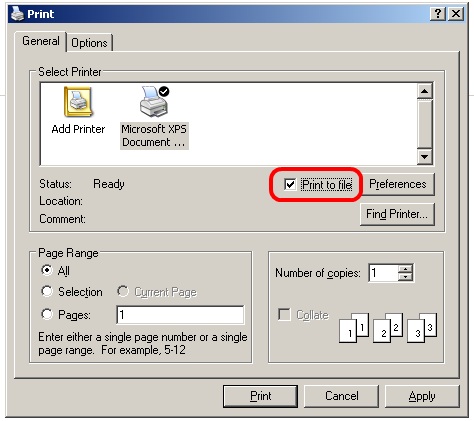
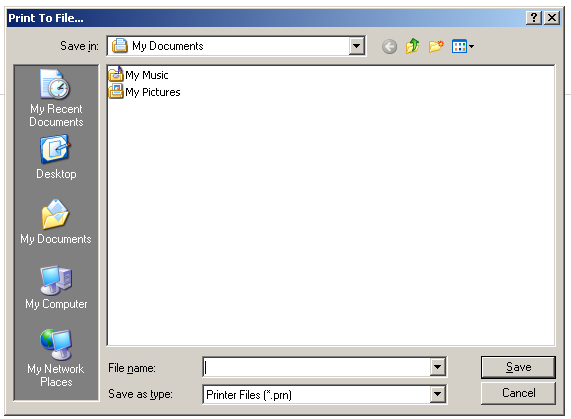
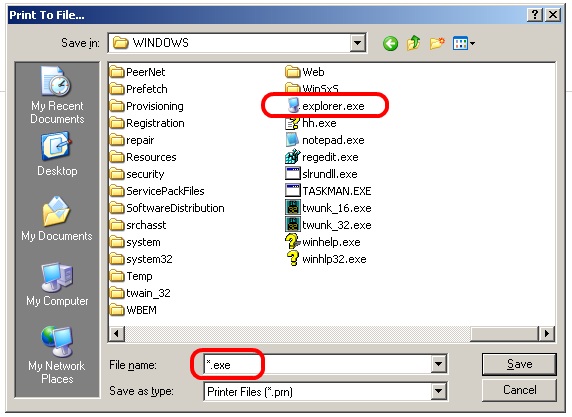
To be able to break out of the malware’s grip we will need to get access to some kind of explorer window. One approach to do this is to get access to a print pop-up. This can be done by pressing Ctrl-P or by selecting some text and pressing the right mouse button, the pop-up will then show the option to print the selected text. In the print pop-up we can select the print to file option, [press print] which then opens an explorer window. The Ctrl-P option might take a while to load and pressing it a couple of times won’t hurt, but the selecting text option seems to work a bit better.
The following screenshots show the steps to take.
Step 2: Replace the malware
Now that we got the above shown window where we can browse files we got (crippled) access to our machine again. The next step is to replace the malware file, we will do this by copying explorer.exe and renaming it to our malware file. This way instead of the malware the system will run explorer.exe on the next boot. To replace the malware we will need to go through the following steps:
- Browse to C:\Windows\
- Type *.exe in the File name field
- Select explorer.exe
- Copy the file by pressing Ctrl-C (the right mouse button doesn’t work very well in this window)
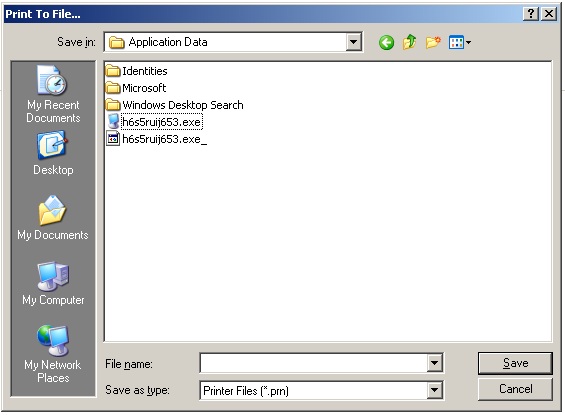
- Browse to the “Application Data” directory of the current user
(for Administrator user: C:\Documents and Settings\Administrator\Application Data\ ) - Paste the copied explorer.exe file by pressing Ctrl-V
- Rename the malware file, just adding an underscore behind is will be enough
- Rename the explorer.exe file to the malware file name
- Reboot
Since we do not have access to the Shutdown controls you need to hold the power button of the system for 7 seconds to turn it off. Then turn the machine back on.
The following screenshots provide some more information to the above named steps.
Step 3: Enable RegEdit
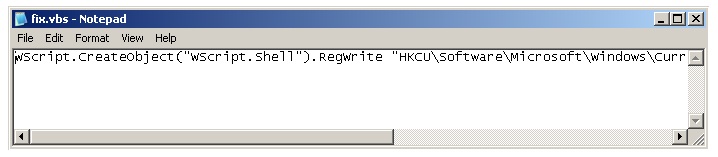
After the reboot we get some slightly less crippled access to the system. However there are still quite some steps to be taken before we can start using Windows normally again. The next step is to enable us to access the Registry again. The malware blocks access to RegEdit and thus also does not allow us to run .reg files, to enable RegEdit again we need access to the Registry so it seems we are stuck here. However, it seems we can access the Registry from other programs or scripts. To enable RegEdit again we will create a small VBS script which changes the registry where RegEdit is blocked. The steps to do this are:
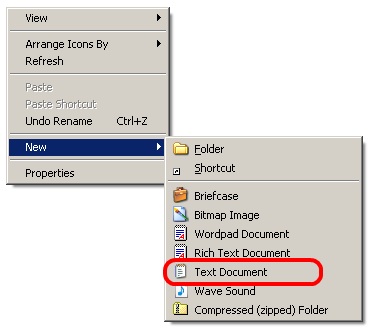
- Create a new file with Right mouse button New –> Text Document
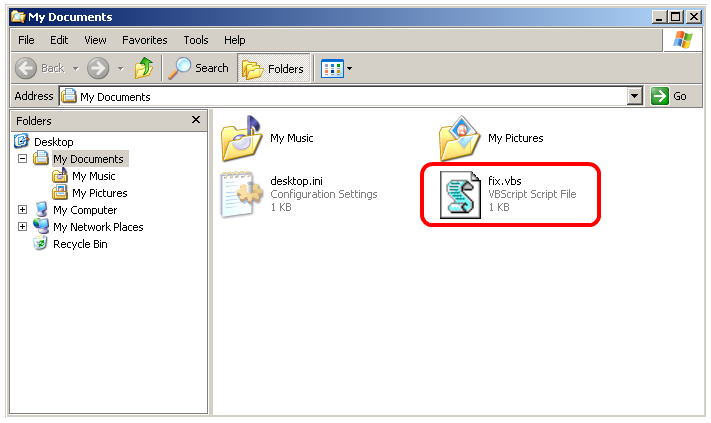
- Name the file fix.vbs
- Edit the file and add the following data to it, make sure it is all on one line, it is only shown here on two lines because of the layout:
WScript.CreateObject("WScript.Shell").RegWrite
"HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System\DisableRegistryTools", 0, "REG_DWORD"
- Save and run the file by double clicking it.
The following screenshots provide some more information to the above named steps.
Step 4: Get full access to Windows
After running the VBS file we can access the Registry again with RegEdit. You can start RegEdit by browsing to the C:\Windows directory and double clicking regedit.exe
Using RegEdit, DELETE the following keys:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\NoDesktop
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System\DisableTaskMgr
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\VX2bt1oYNKCLnkO
- HKEY_USERS\Administrator\Software\Microsoft\Windows\Current Version\Policies\Explorer\NoDesktop
- HKEY_USERS\Administrator\Software\Microsoft\Windows\Current Version\Policies\System\DisableTaskMgr
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run\VX2bt1oYNKCLnkO
Then CHANGE the following keys:
- HKEY_CURRENT_USER\Software\Microsoft\Windows NT\Current Version\Winlogon
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\Current Version\Winlogon
Change the value of “Userinit” to “C:\Windows\System32\Userinit.exe,”
Change the value of “Shell” to “Explorer.exe”
With different versions of the malware the Registry locations might be different than displayed above. The best way to search for any remaining registry information set by the malware is to search for the malware name.
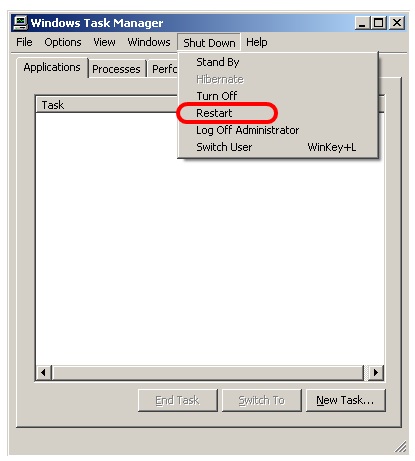
After all these changes reboot the system, this can be done by bringing up the Task Manager (which has now been enabled again) with Ctrl-Shift-Esc and then choose Shutdown and then Restart.
Step 5: Clean your system
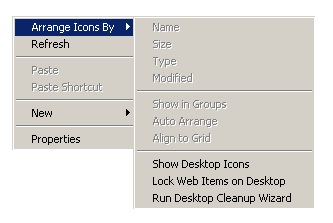
After the reboot you got full access to the system again, however your Desktop will still be empty, to get the Desktop items back click the right mouse button on the desktop and select Arrange Icons By and then Show Desktop Icons.
 The next thing to do is scan your whole system for any remaining malware. Microsoft Security Essentials for example recognizes this specific malware since March 2, 2012, so it should be able to remove the malware files. I would still recommend to do a full reinstall of the system after you recovered all your data, malware often does not come alone. Since the malware might have infected your system by a Drive-By Download it makes sense to make sure all your software is up to date (pay special attention to Windows Update, Adobe Flash, Adobe PDF Reader and Java). This might also be a good moment to start thinking about creating some backups 😉
The next thing to do is scan your whole system for any remaining malware. Microsoft Security Essentials for example recognizes this specific malware since March 2, 2012, so it should be able to remove the malware files. I would still recommend to do a full reinstall of the system after you recovered all your data, malware often does not come alone. Since the malware might have infected your system by a Drive-By Download it makes sense to make sure all your software is up to date (pay special attention to Windows Update, Adobe Flash, Adobe PDF Reader and Java). This might also be a good moment to start thinking about creating some backups 😉
Video of the whole process
Update May 2012
It seems that the malware is now targeting other countries as well besides the Netherlands, it now also fakes to be from the following parties:
- SUISA (Switzerland)
- GVU (Germany)
- AKM (Austria)
- PRS (United Kingdom)
- SACEM (France)
More info can be found on abuse.ch: http://www.abuse.ch/?p=3718
Buma Stermra Virus verwijderen, malware, ransomware, ransom-ware, computer, PC, gelockt, gelocked, geblokkeerd, politie. BUMA-STEMRA (Netherlands) SUISAÂ Â (Swiztzerland) GVU (Germany) AKM (Austria) PRSÂ (United Kingdom)Â SACEM (France) locked PC, remove malware, get rid off malware, malware removal,

Leave a Reply